Import Containers
Recommended for Technical Users
This method requires use of a Command Line Interface and knowledge of your codebase. If you're not a developer yourself, we recommend getting a developer to help you
Overview
Container scanning helps you mitigate open source risk by identifying vulnerability and license issues in your container images.
Supported Base Containers
FOSSA's container scanning supports most popular base images, and any containers that use those base images. Please find our complete list of supported base containers below:
| Package Manager | Distribution |
|---|---|
| Apt / Apt-Get | Debian, Ubuntu |
| RPM / Yum | Redhat, Centos, Oraclelinux, Fedora, SLES (in beta) |
| Apk | Alpine |
It's possible distributions not listed here will analyze successfully, but it's not guaranteed.
Getting started
Container Scanning follows existing FOSSA CLI convention and should be intuitive if you're familiar with the tool. For additional information on FOSSA CLI you can find our documentation on GitHub.
To run a scan :
FOSSA_API_KEY=<your_api_key>
fossa container analyze <your image: docker|oci.tar>
It may take a minute to run, if your images are large.
Running a scan will look like this:
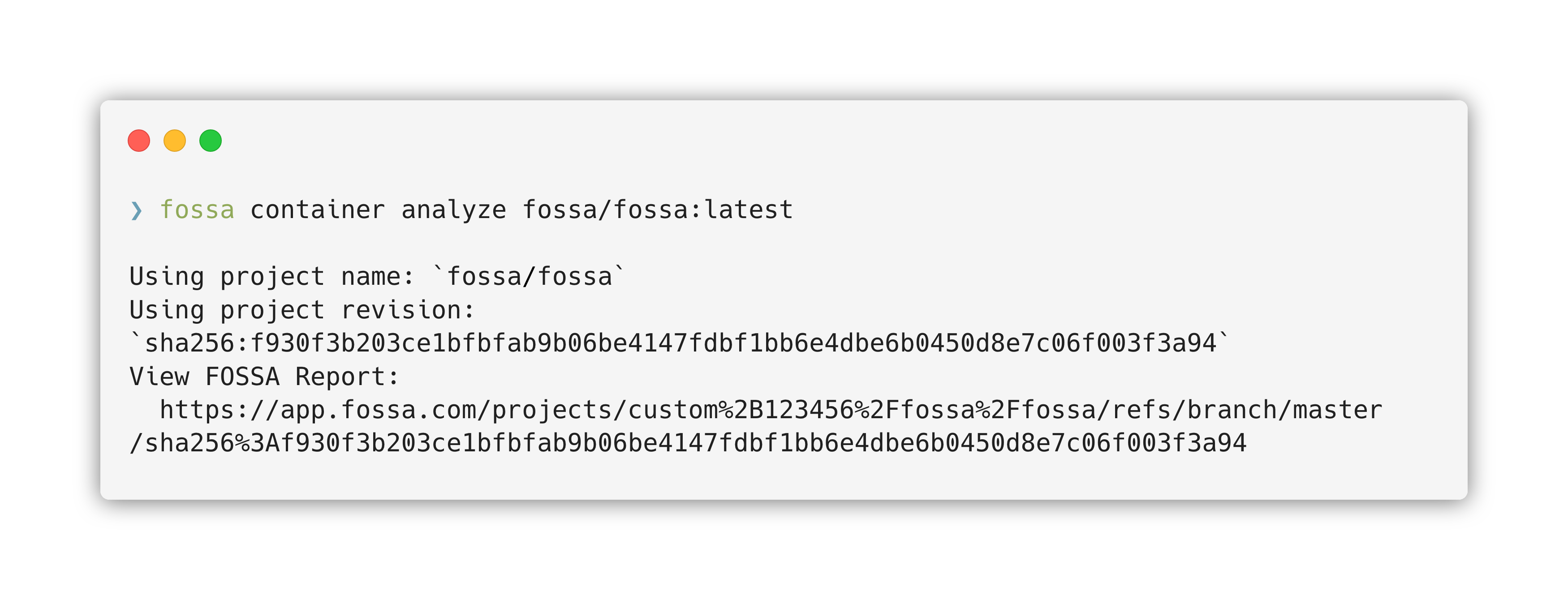
Container scanning will take any arguments fossa analyze is able too, such as, --title, --team, and --policy. To see a full list of these arguments you can use fossa container analyze --help or you can find our documentation on GitHub.
Where do we get your images from?
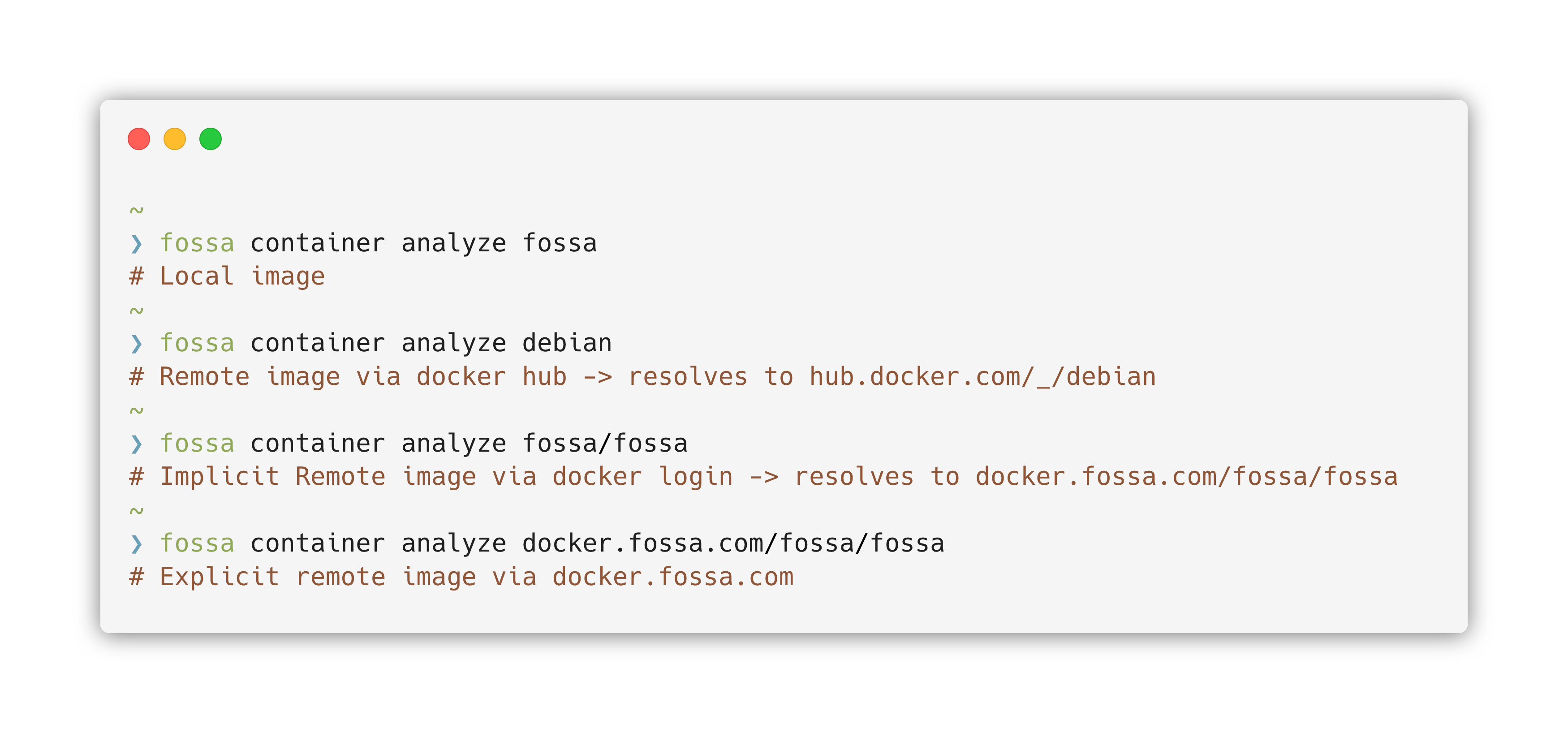
FOSSA is able to ingest either docker images - straight from your local docker application, or an OCI formatted image archive. No arguments are required to specify which kind of image you are using.
FOSSA will also be able to use any remote or private docker registries through dockers native authentication path using docker login.
Using docker images and registries
FOSSA uses docker to pull local and remote images easily and securely. When provided a docker image name, FOSSA CLI will request the image from the Docker application and begin to parse it.
FOSSA will accept images in exactly the same format as docker pull. Like docker, FOSSA will first attempt to pull images from your local docker repository, then from docker hub, then from any registries you've logged into. FOSSA will also accept images directly from a repository. For example, fossa container analyze quay.io/coreos/dnsmasq
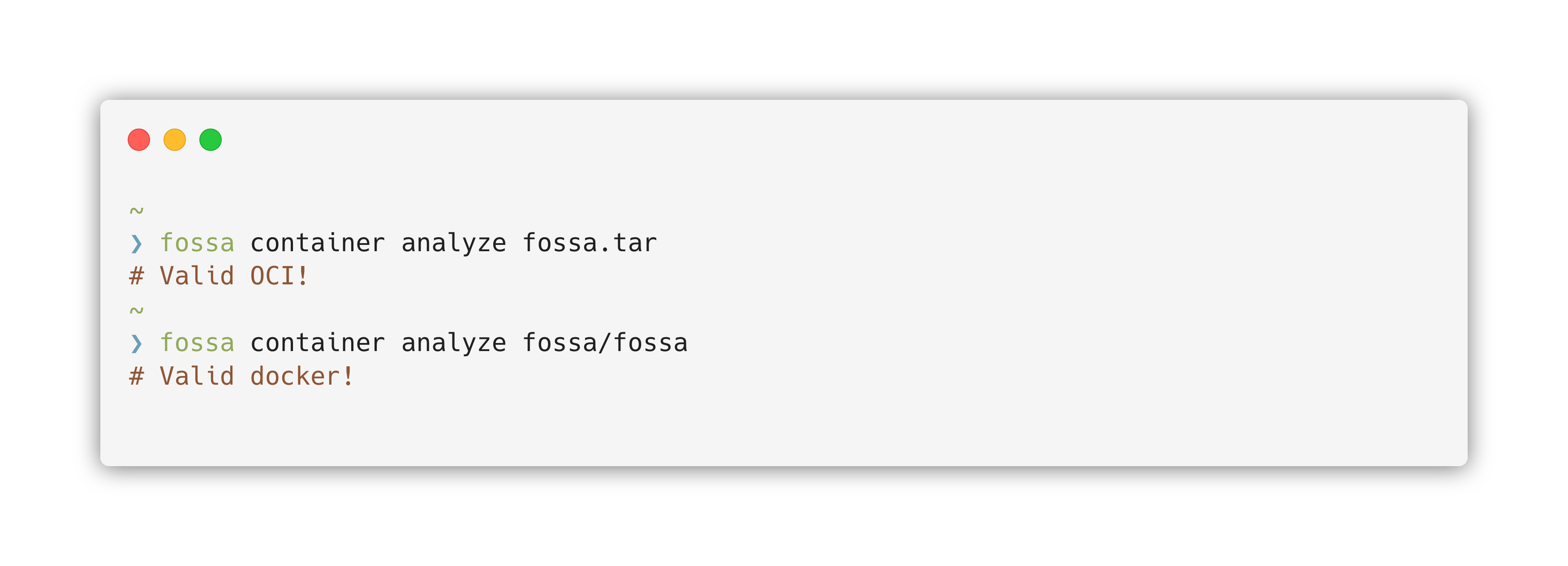
Using OCI images
FOSSA supports OCI (Open Container Initiative) formatted images on your file system natively. OCI images can be generated from docker by using docker image save or by using your favorite image infrastructure such as Packer or Buildah.
Once you have an image, you may scan your OCI image just as you would a docker image in FOSSA.

Updated 6 months ago
