Generating SBOMs
SBOM Generation
In response to EO 14028 many organizations, both public and private sector, require software producers to generate Software Bill of Materials (SBOMs) to improve supply chain risk management. To comply with these obligations, you can generate SBOMs automatically using FOSSA.
These documents not only disclose open source component usage and their associated metadata but are useful for a number of events:
- Security vulnerability reviews and VDR(Vulnerability Disclosure Report)/VEX(Vulnerability Exploitability eXchange) communication
- Customer-facing Bill-of-Materials for sales enablement, partnerships or OEMs
- Fully-compliant attribution and copyright notices
- End of X (Life, Support, Maintenance) communication
To see an example live of how one of our customers uses FOSSA's reports, check out CNCF's Public SBOM Portal.
Software Bill of Material (SBOM) Generation via CLI
The FOSSA CLI, as of v3.1.5, is also capable of generating SBOM reports. This can be useful if you want to automate report generation in your CI pipeline. The FOSSA CLI currently supports four different formats: JSON, SPDX, markdown, and text. In order to generate a report in the FOSSA CLI you will need to run an additional report command after analyzing your project. The flags json, spdx, markdown, or text control the output format. Example:
export FOSSA_API_KEY=XXXXXXXX
fossa analyze && fossa report attribution --format spdxExample truncated SPDX report from the FOSSA CLI:
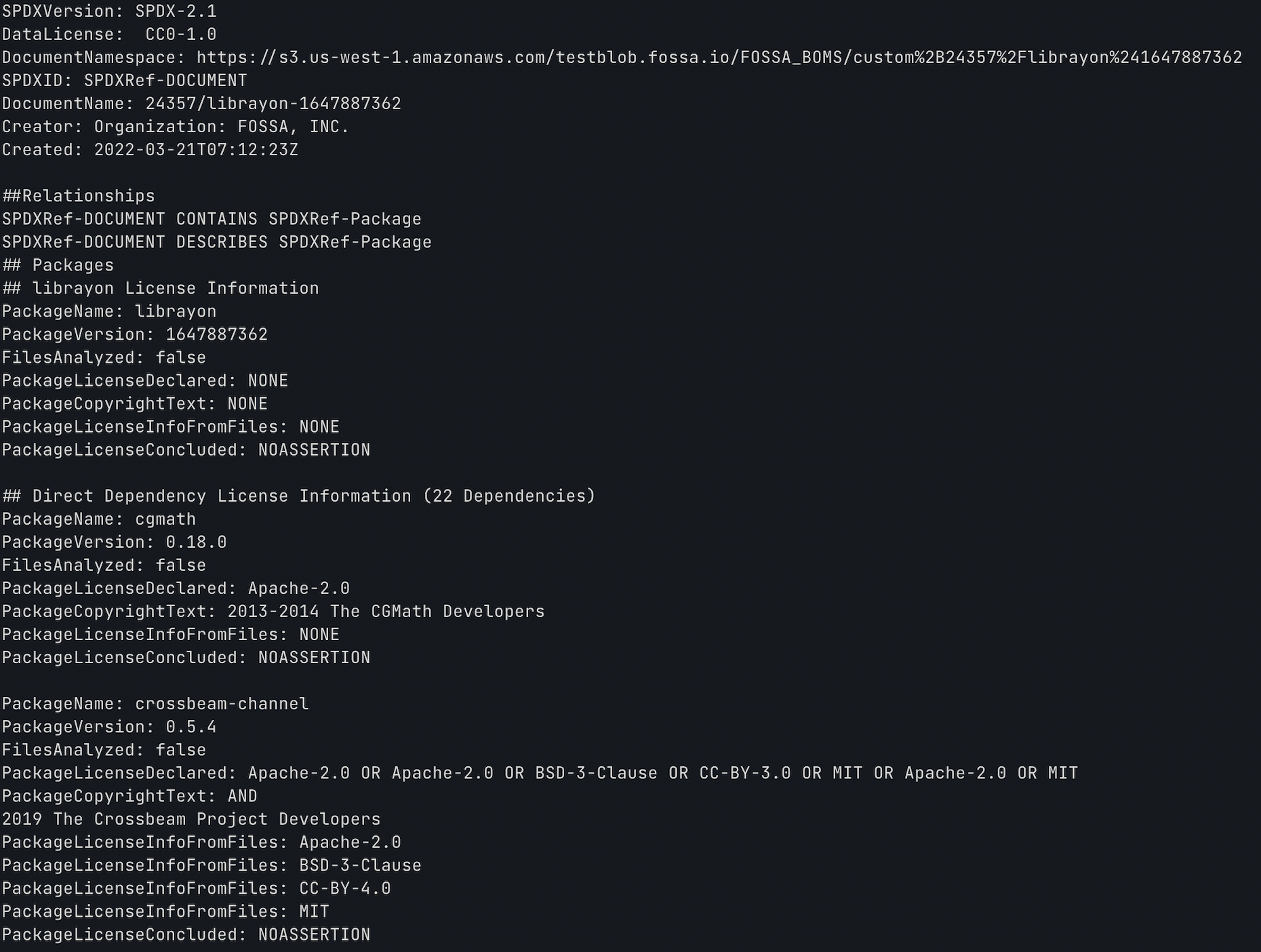
Generating Software Bill of Materials (SBOMs) via UI
Visit a project or release group page and navigate to the Reports > SBOM tab to get to the SBOM Generation Tool:
On this page, you can choose which SBOM specification (cycloneDX or spdx) as well as your desired format (json , xml, tag-value) and preview what your SBOM will look like.
Embedding VDR & VEX statements:
FOSSA can help you automatically generate VDR and VEX statements within your SBOMs based on the security issue status for a given project or release group.
Selecting vulnerabilities within the applicable SBOM format will embed a VDR & VEX statement. Doing so adds a vulnerabilites array to your supported SBOM format.
All active security issues will be embedded with their CVE metadata (VDR) and an analysis (VEX) affirming the state is affected.
All ignored security issues will be embedded with their CVE metadata (VDR) and an analysis (VEX) affirming the state is not_affected , and an applicable justification. The justification is based on the CISA compliant VEX justifications . Pease see the below table of security ignore reasons and CISA VEX justification mappings:
| FOSSA Ignore Reason | CISA VEX justification | VEX Supported |
|---|---|---|
| Component not present | Component_not_present | Yes |
| Inline mitigation already exists | Inline_mitigations_already_exist | Yes |
| Vulnerable code cannot be controlled by adversary | Vulnerable_code_cannot_be_controlled_by_adversary | Yes |
| Vulnerable code not in execute path | Vulnerable_code_not_in_execute_path | Yes |
| Incorrect data found | N/A | No |
| Other | N/A | No |
Example VDR & VEX statement
"vulnerabilities": [
{
"bom-ref": "CVE-2023-39956",
"id": "CVE-2023-39956",
"source": {
"url": "https://nvd.nist.gov/vuln/detail/CVE-2023-39956",
"name": "NVD"
},
"ratings": [
{
"source": {
"url": "https://nvd.nist.gov/vuln/detail/CVE-2023-39956",
"name": "NVD"
},
"score": 6.6,
"severity": "medium",
"vector": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:H/A:L",
"method": "CVSSv31"
}
],
"cwes": [
94
],
"description": "Electron is a framework which lets you write cross-platform desktop applications using JavaScript, HTML and CSS. Electron apps that are launched as command line executables are impacted. Specifically this issue can only be exploited if the following conditions are met: 1. The app is launched with an attacker-controlled working directory and 2. The attacker has the ability to write files to that working directory. This makes the risk quite low, in fact normally issues of this kind are considered outside of our threat model as similar to Chromium we exclude Physically Local Attacks but given the ability for this issue to bypass certain protections like ASAR Integrity it is being treated with higher importance. This issue has been fixed in versions:`26.0.0-beta.13`, `25.4.1`, `24.7.1`, `23.3.13`, and `22.3.19`. There are no app side workarounds, users must update to a patched version of Electron.",
"recommendation": "Upgrade dependency electron from version 11.1.1 to 22.3.21 to mitigate this vulnerability, or to version 22.3.25 to mitigate all existing vulnerabilities.",
"advisories": [
{
"url": "https://github.com/electron/electron/security/advisories/GHSA-7x97-j373-85x5"
},
{
"url": "https://github.com/advisories/GHSA-7x97-j373-85x5"
},
{
"url": "https://www.npmjs.com/package/electron"
}
],
"published": "2023-09-06T19:51:33.000Z",
"affects": [
{
"ref": "pkg:npm/[email protected]",
"versions": [
{
"version": "11.1.1",
"status": "affected"
}
]
}
],
"analysis": {
"state": "not_affected",
"justification": "Inline_mitigations_already_exist",
"detail": "Dev Analysis: CVE not exploitable due to inline mitigation in the form of external input validation preventing injection"
}
},
{
"bom-ref": "CVE-2023-44402",
"id": "CVE-2023-44402",
"source": {
"url": "https://nvd.nist.gov/vuln/detail/CVE-2023-44402",
"name": "NVD"
},
"ratings": [
{
"source": {
"url": "https://nvd.nist.gov/vuln/detail/CVE-2023-44402",
"name": "NVD"
},
"score": 7,
"severity": "high",
"vector": "CVSS:3.1/AV:L/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H",
"method": "CVSSv31"
}
],
"cwes": [
345
],
"description": "Electron is an open source framework for writing cross-platform desktop applications using JavaScript, HTML and CSS. This only impacts apps that have the `embeddedAsarIntegrityValidation` and `onlyLoadAppFromAsar` fuses enabled. Apps without these fuses enabled are not impacted. This issue is specific to macOS as these fuses are only currently supported on macOS. Specifically this issue can only be exploited if your app is launched from a filesystem the attacker has write access too. i.e. the ability to edit files inside the `.app` bundle on macOS which these fuses are supposed to protect against. There are no app side workarounds, you must update to a patched version of Electron.",
"recommendation": "Upgrade dependency electron from version 11.1.1 to 22.3.24 to mitigate this vulnerability, or to version 22.3.25 to mitigate all existing vulnerabilities.",
"advisories": [
{
"url": "https://github.com/electron/electron/security/advisories/GHSA-7m48-wc93-9g85"
},
{
"url": "https://github.com/advisories/GHSA-7m48-wc93-9g85"
},
{
"url": "https://www.npmjs.com/package/electron"
},
{
"url": "https://github.com/electron/electron/pull/39788"
},
{
"url": "https://www.electronjs.org/docs/latest/tutorial/fuses"
}
],
"published": "2023-12-01T21:32:06.000Z",
"affects": [
{
"ref": "pkg:npm/[email protected]",
"versions": [
{
"version": "11.1.1",
"status": "affected"
}
]
}
],
"analysis": {
"state": "affected"
}
},
{
"bom-ref": "CVE-2023-29198",
"id": "CVE-2023-29198",
"source": {
"url": "https://nvd.nist.gov/vuln/detail/CVE-2023-29198",
"name": "NVD"
},
"ratings": [
{
"source": {
"url": "https://nvd.nist.gov/vuln/detail/CVE-2023-29198",
"name": "NVD"
},
"score": 8.5,
"severity": "high",
"vector": "CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:H/I:H/A:H",
"method": "CVSSv31"
}
],
"cwes": [
754
],
"description": "Electron is a framework which lets you write cross-platform desktop applications using JavaScript, HTML and CSS. Electron apps using `contextIsolation` and `contextBridge` are affected. This is a context isolation bypass, meaning that code running in the main world context in the renderer can reach into the isolated Electron context and perform privileged actions. This issue is only exploitable if an API exposed to the main world via `contextBridge` can return an object or array that contains a javascript object which cannot be serialized, for instance, a canvas rendering context. This would normally result in an exception being thrown `Error: object could not be cloned`. The app side workaround is to ensure that such a case is not possible. Ensure all values returned from a function exposed over the context bridge are supported. This issue has been fixed in versions `25.0.0-alpha.2`, `24.0.1`, `23.2.3`, and `22.3.6`.",
"recommendation": "Upgrade dependency electron from version 11.1.1 to 22.3.6 to mitigate this vulnerability, or to version 22.3.25 to mitigate all existing vulnerabilities.",
"advisories": [
{
"url": "https://github.com/electron/electron/security/advisories/GHSA-p7v2-p9m8-qqg7"
},
{
"url": "https://github.com/advisories/GHSA-p7v2-p9m8-qqg7"
},
{
"url": "https://www.npmjs.com/package/electron"
},
{
"url": "https://www.electronjs.org/docs/latest/api/context-bridge#parameter--error--return-type-support"
}
],
"published": "2023-09-06T19:50:58.000Z",
"affects": [
{
"ref": "pkg:npm/[email protected]",
"versions": [
{
"version": "11.1.1",
"status": "affected"
}
]
}
],
"analysis": {
"state": "affected"
}
}
Premium FeatureBusiness and Enterprise feature only. Please contact [email protected] for more details.
Customizing a Software Bill of Materials
Step 1: Select Your Reporting Format
FOSSA supports multiple SBOM formats: **CycloneDX-json, CycloneDX-xml, SPDX-tag-vaue, SPDX-json.
Step 2: Select the Components of Your Report
FOSSA offers the ability to customize the types of information displayed. Within the Reports tab you can decide whether you want to include.
Step 3: Select the Open Source Package Information to Include
FOSSA collects information about every open source component including information like the package authors, the package URL, and more. You can customize the information about each open source component by clicking edit dependency information. The following information is available:
| Property | Description | Specification Supported |
|---|---|---|
| Authors | Selecting authors displays the creators of the package. In most cases, this information is pulled from the package registry. | cycloneDX or spdx |
| Description | Selecting description includes information regarding what the package's functionality is. In most cases, this information is pulled from the package registry. | cycloneDX or spdx |
| Package Homepage | Selecting package homepage includes the link package's homepage whether it is a Github repo, stand-a-lone website, or hosted by a package manager. | spdx |
| File Matches | The list of file locations by which a particular license match was detected | spdx |
| Vulnerabilities | The Vulnerability Disclosure Report and Vulnerability Exploitability eXchange information for security issues | cycloneDX |
| Support Status | The "maintained" or "abandoned" status for a given package. The "abandoned" status requires FOSSA quality policy with "abandonware" Risk intelligence signals enabled. See abandonware for more details | cycloneDX |
NoteCurrently all direct and transitive dependencies are included in all SBOM formats
Example support status outputs
Abandoned package
"purl": "pkg:npm/[email protected]",
"properties": [
{
"name": "support status",
"value": "abandoned"
}
]Maintained package
"purl": "pkg:npm/[email protected]",
"properties": [
{
"name": "support status",
"value": "maintained"
}
]Step 4
Select Download or Email to download the SBOM or start the generation job to email the SBOM depending on the dependency count and size.
For more questions please contact [email protected]
Updated 7 months ago
