Active Directory Federation Service
To configure Active Directory Federation Service (ADFS) for single sign on to FOSSA, we need to create a Relying Party Trust on ADFS. To get started, open the Server Manager then choose Tools → AD FS Management.
In the AD FS Management tool, click "Add Relying Party Trust".
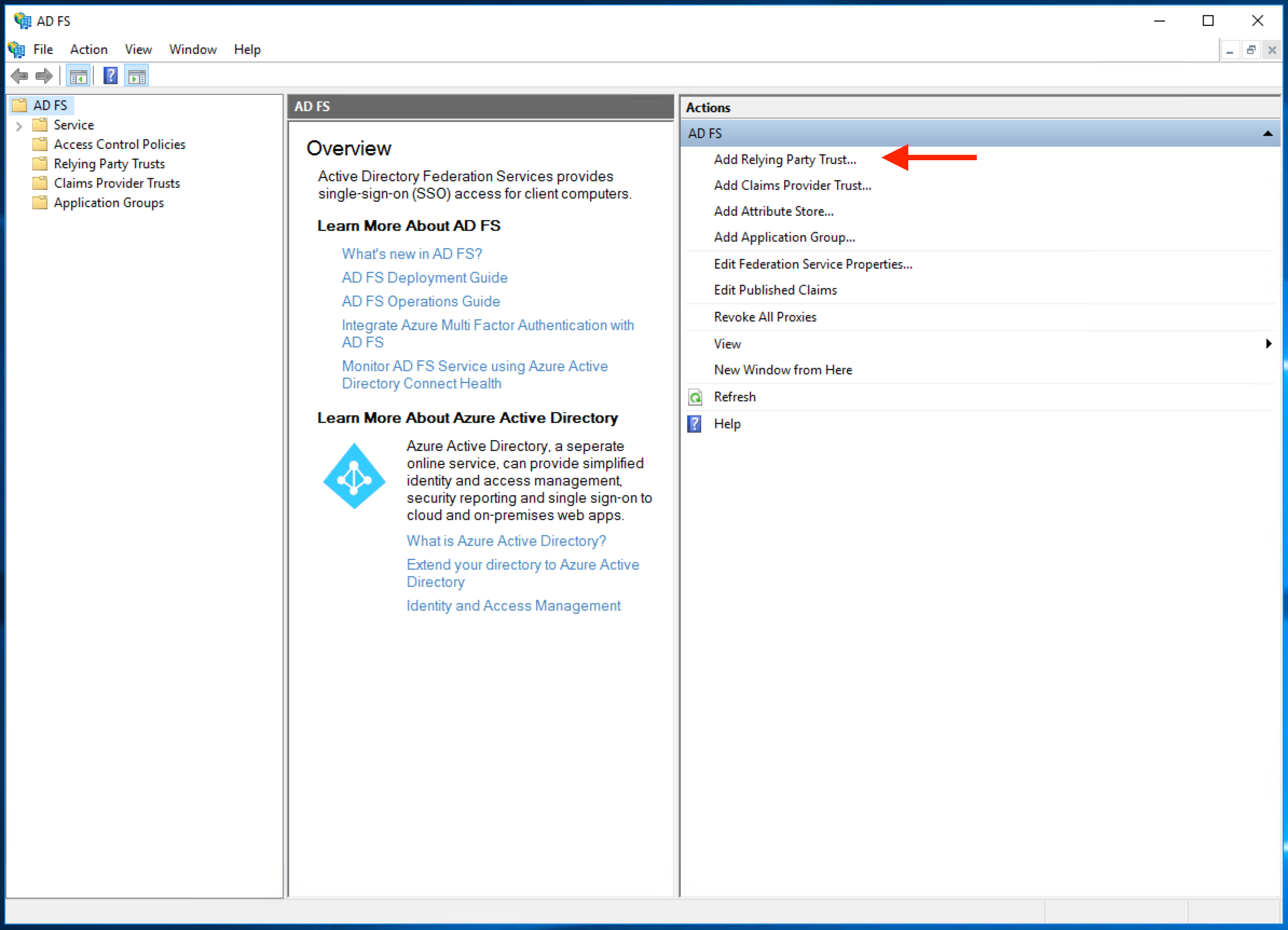
This will open a wizard. Select "Claims aware" and click "Start".
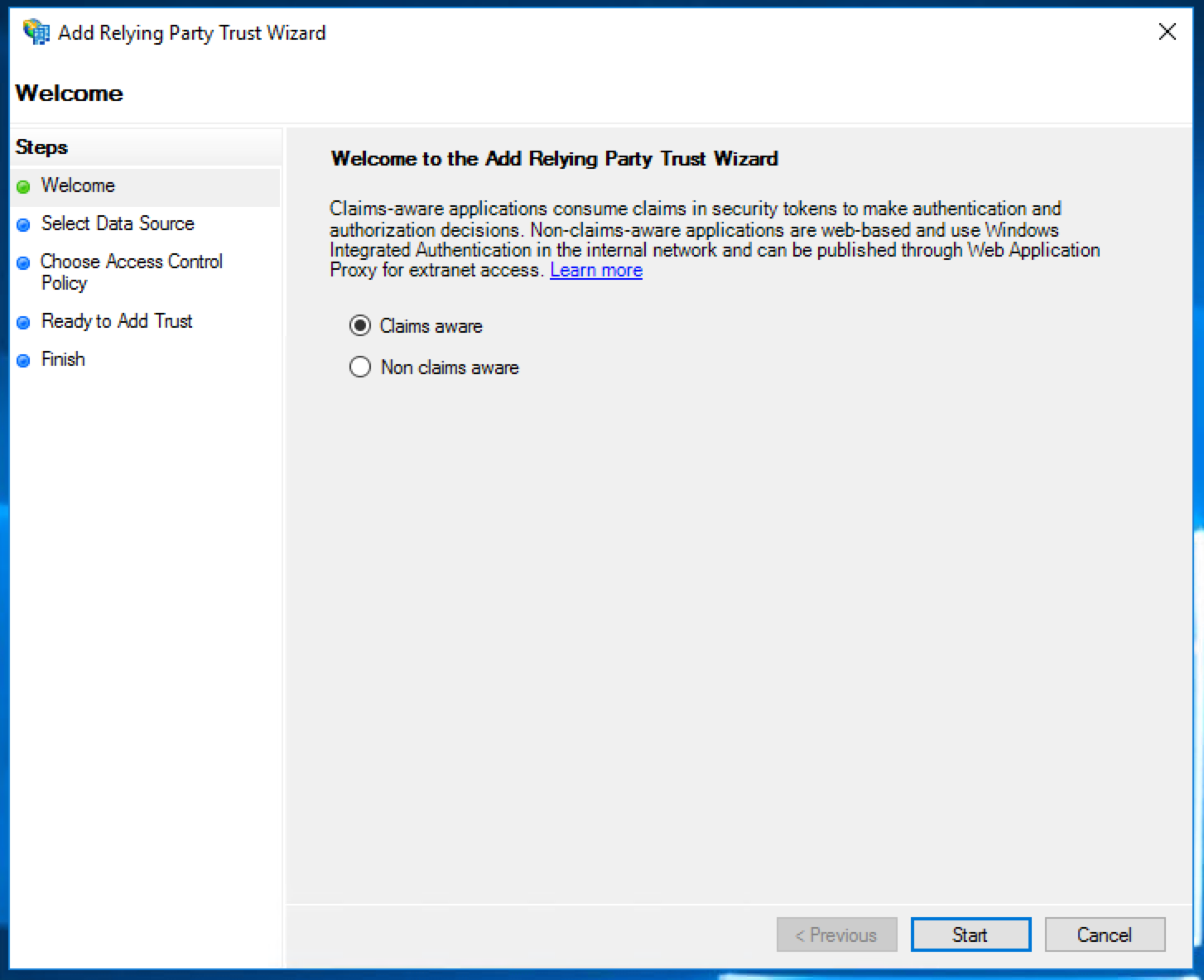
Select the option to enter data about the relying party manually.
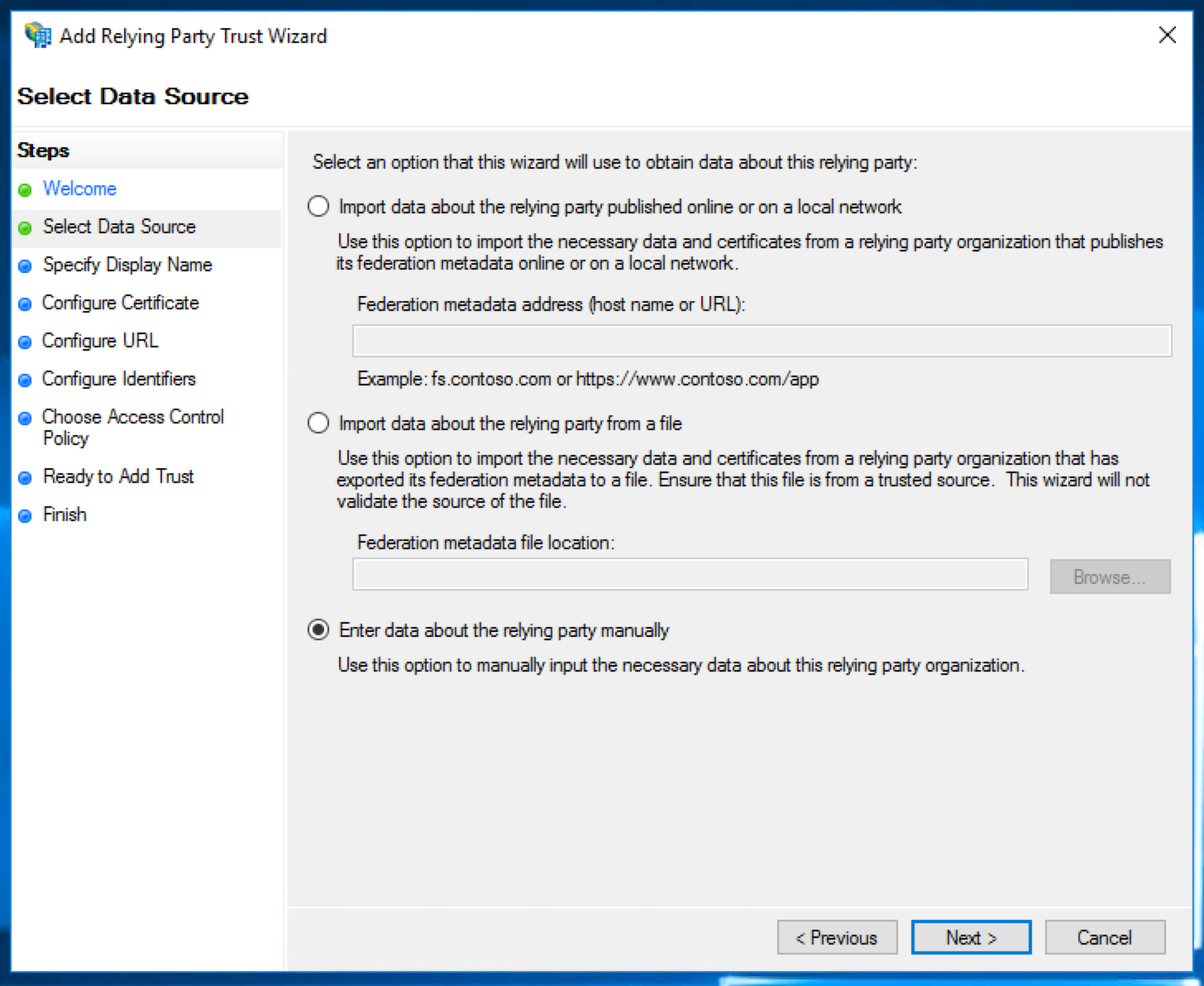
Tick the box to "Enable support for the SAML 2.0 WebSSO protocol". In the text box underneath, fill in the "Callback URL" from the SAML settings page on FOSSA.
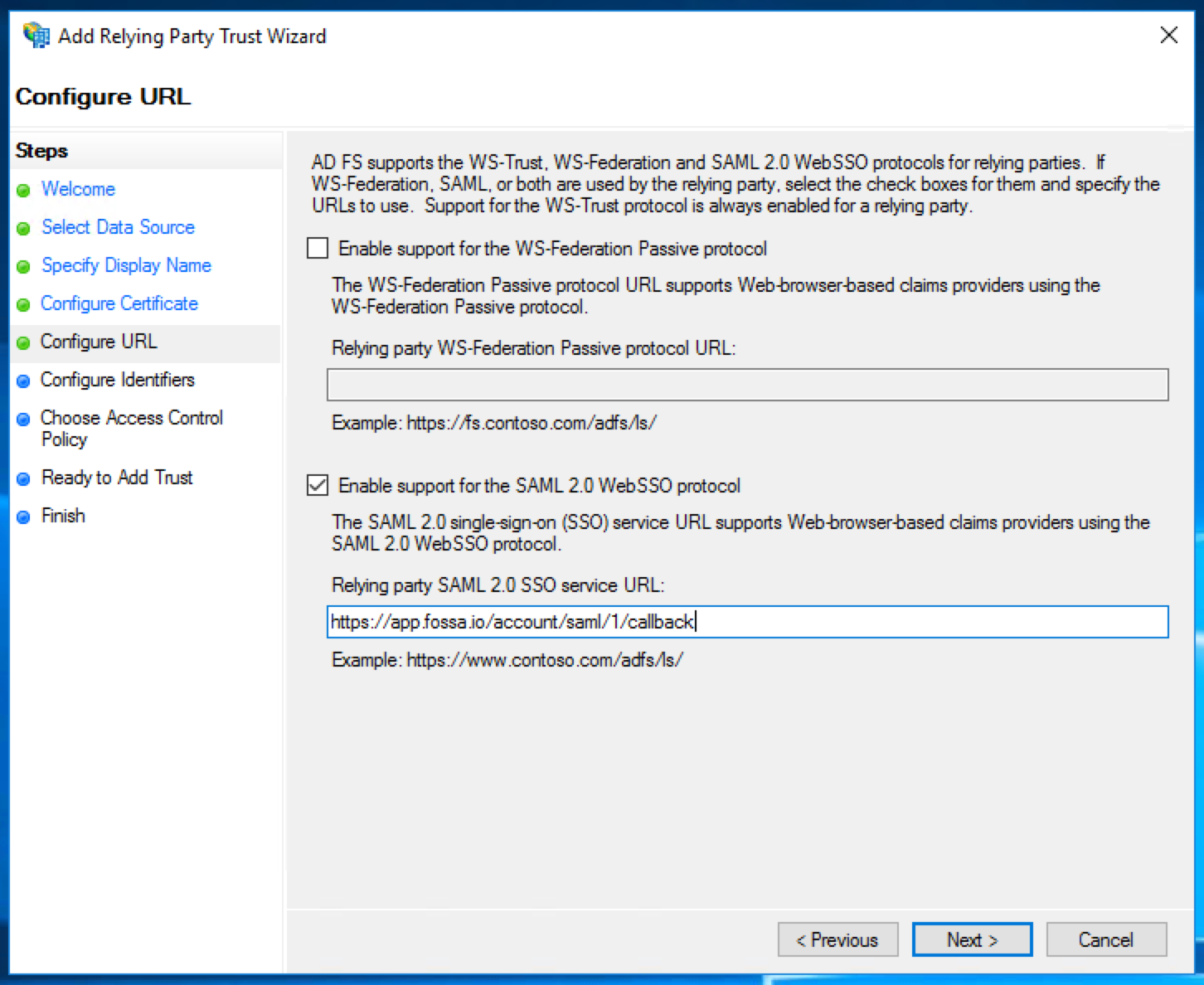
Add the relying party trust identifier "FOSSA".
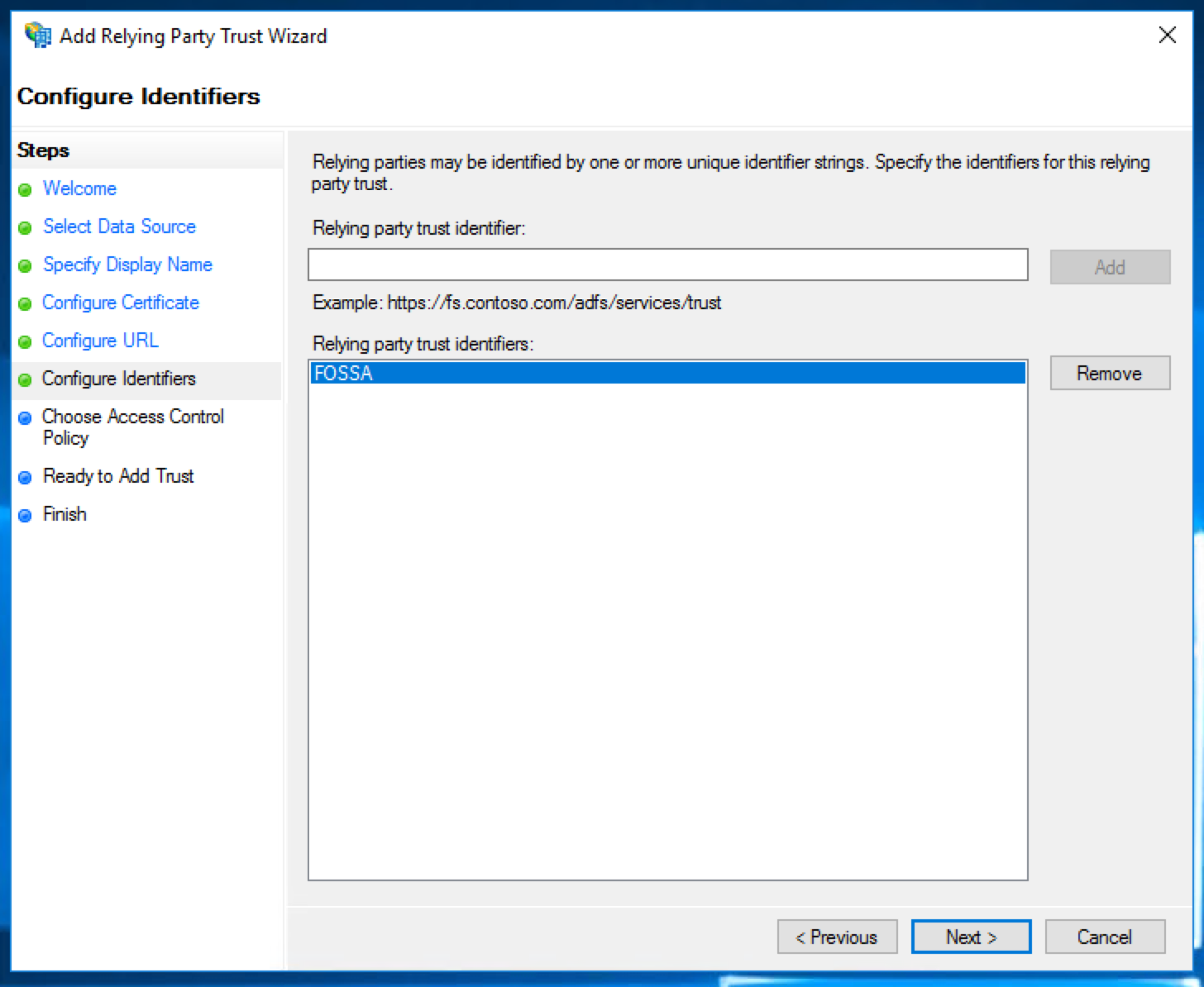
Tick the option to "Configure claims issuance policy for this application".
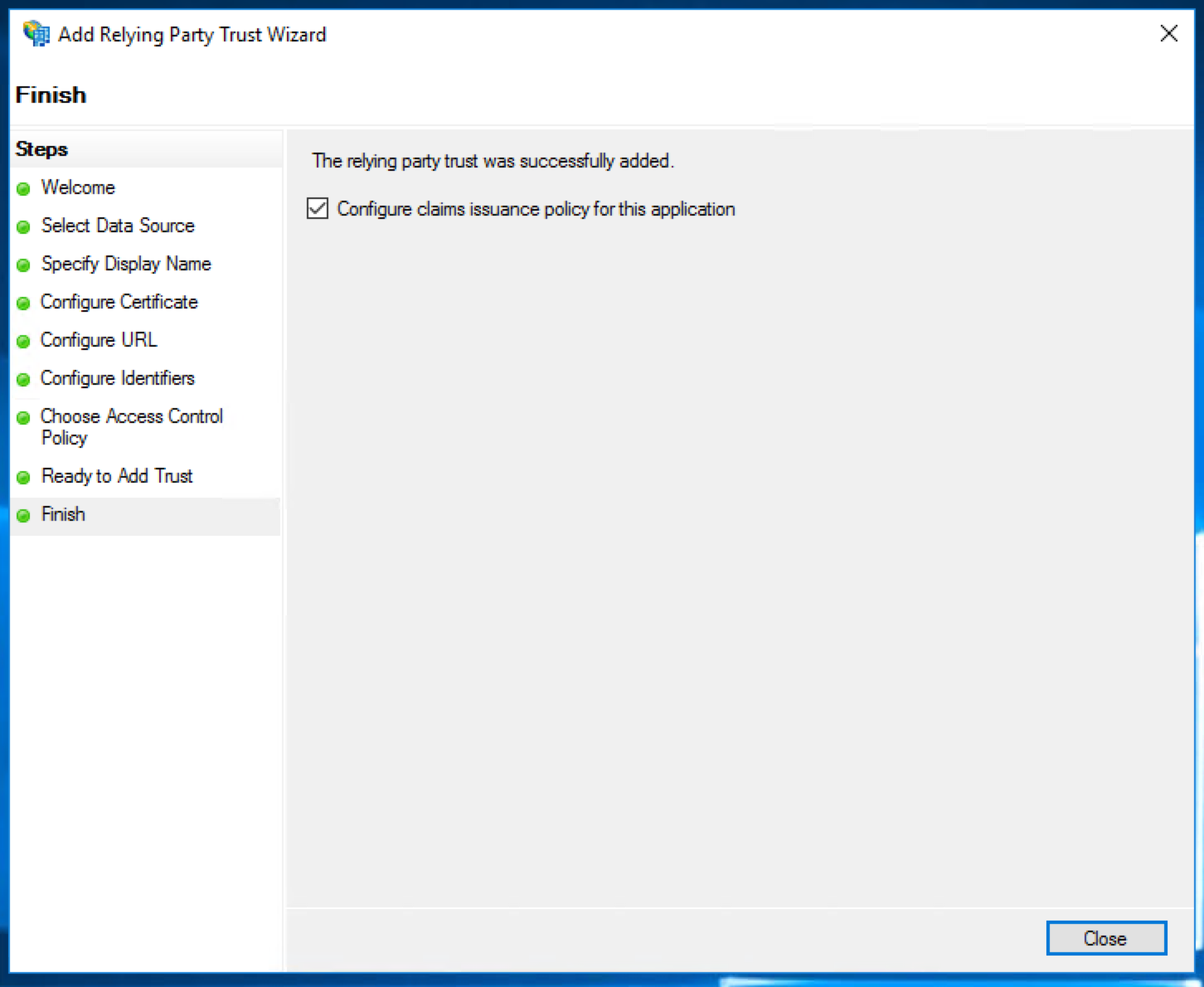
This will open a new wizard which will configure what data is sent from Active Directory to FOSSA as part of the log in process. Click "Add Rule".
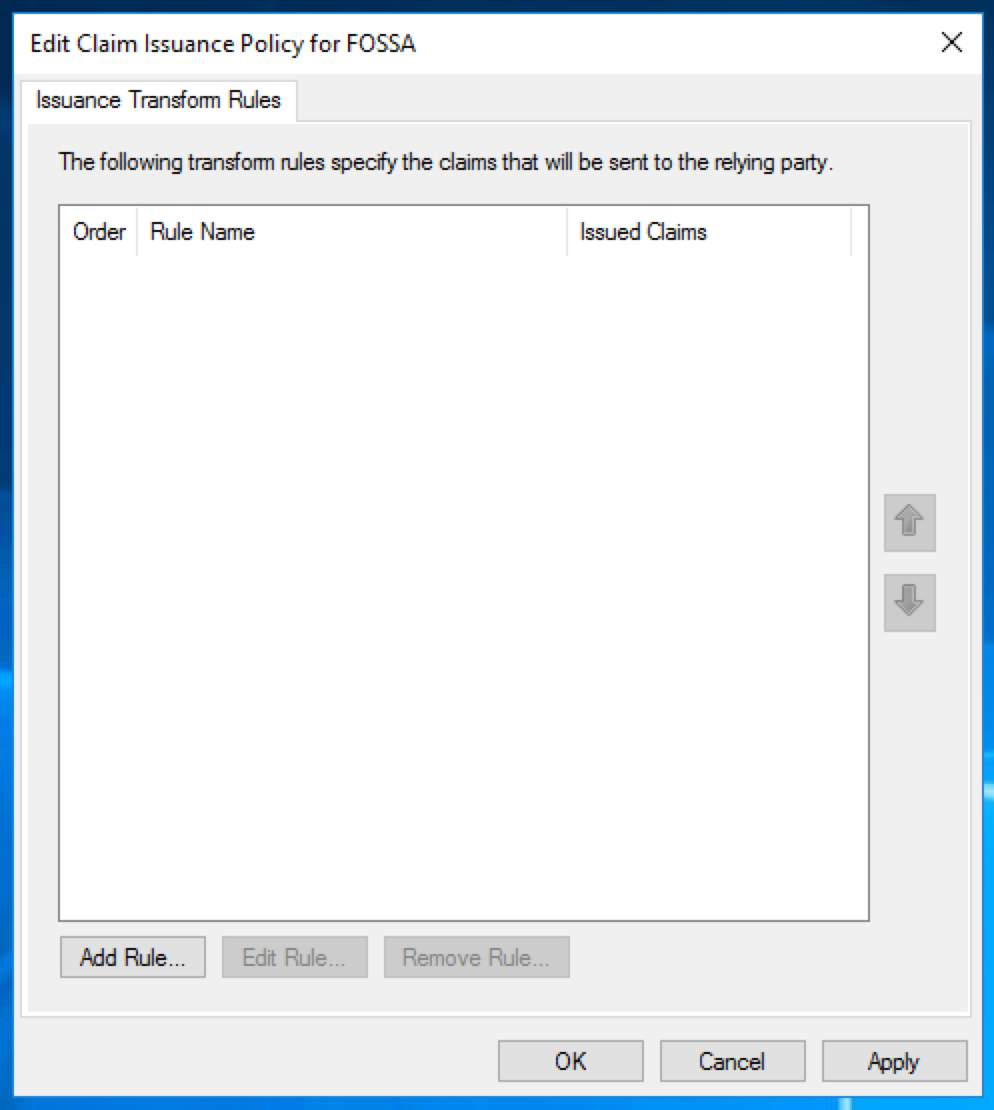
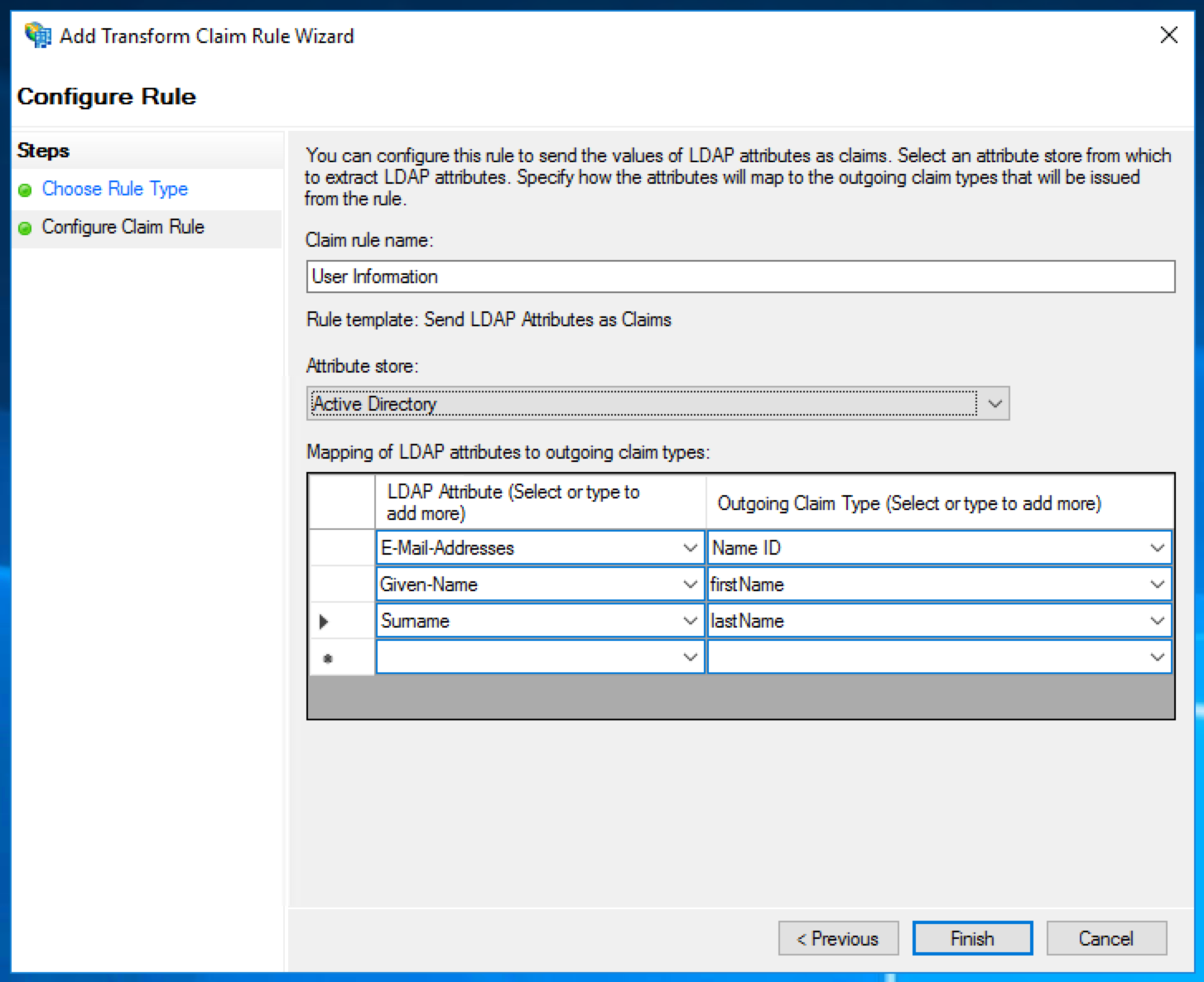
Choose the claim rule template "Send LDAP Attributes as Claims".
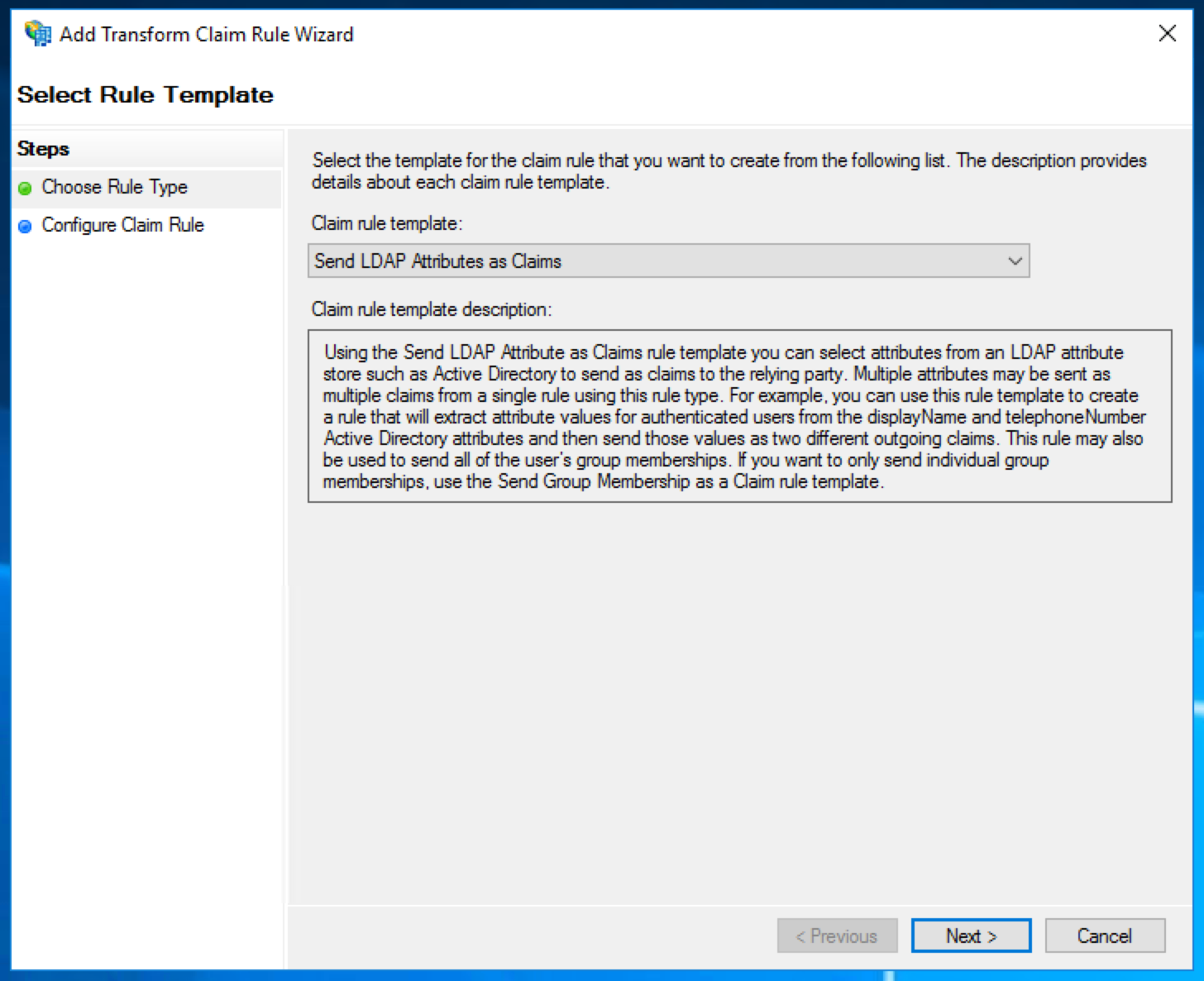
Give the rule an informative name, choose "Active Directory" as the attribute store, and add the following mappings:
LDAP Attribute | Outgoing Claim Type |
|---|---|
E-Mail-Addresses | Name ID |
Given-Name | firstName |
Surname | lastName |
Active Directory Federation Service is now configured to authenticate users to FOSSA.
To finish setting up FOSSA, we need to get a copy of the ADFS Token Signing Certificate. Back in the AD FS Management tool, click Service → Certificates in the left sidebar, select the token signing certificate, then click "View Certificate" in the right sidebar.
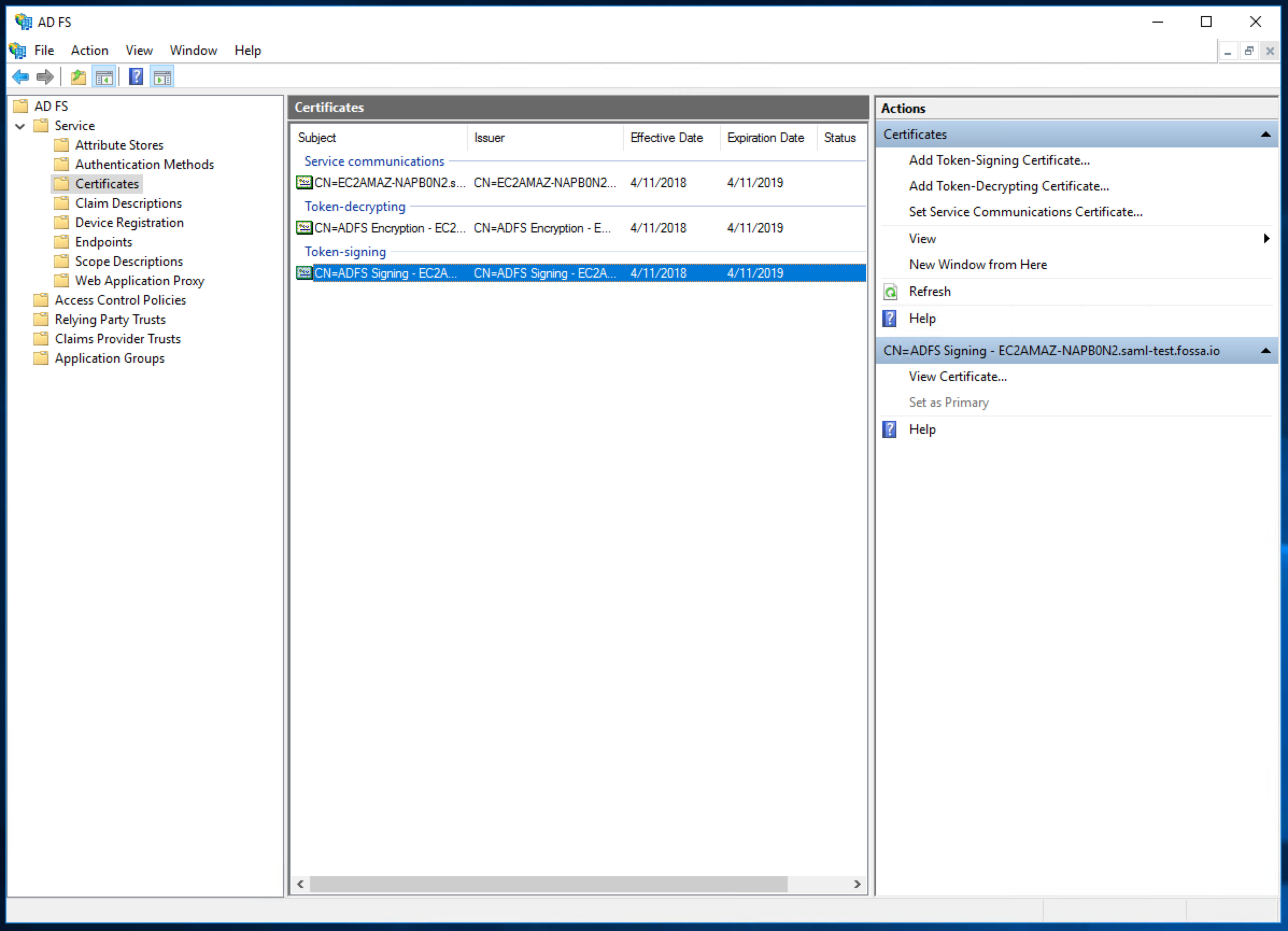
Click the "Details" tab along the top, then "Copy to File" at the bottom.
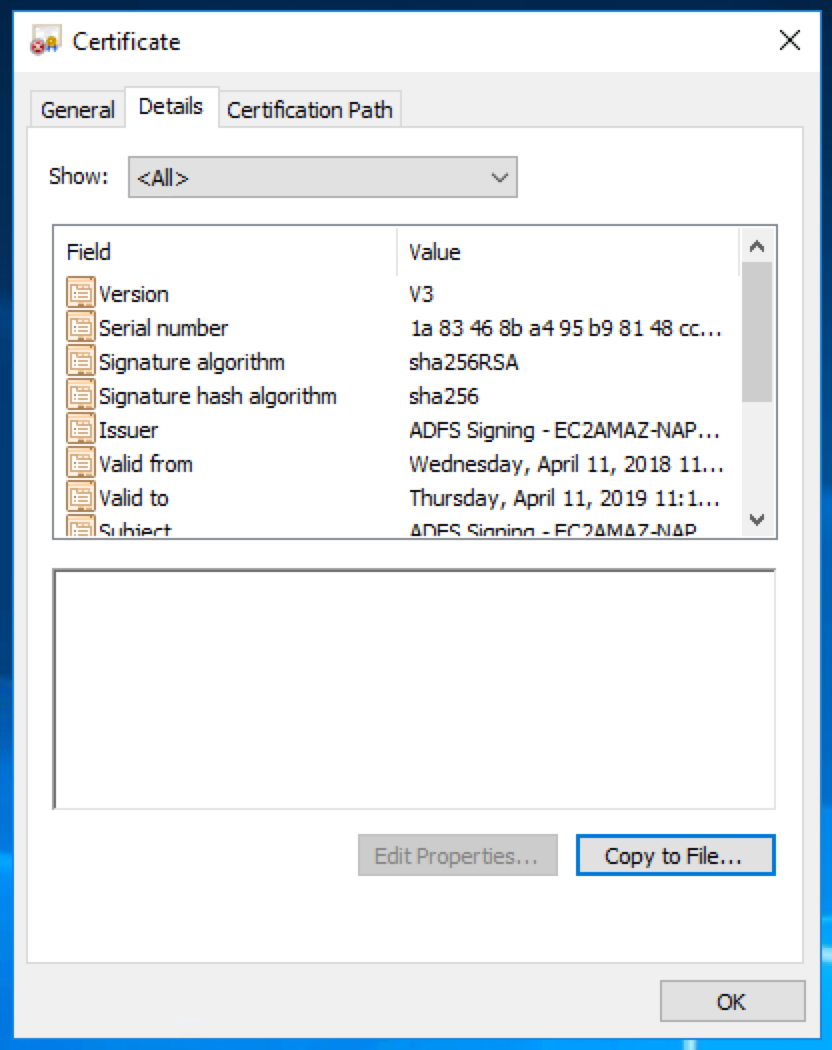
Choose to export the certificate as "Base-64 encoded X.509 (.CER)"
Open the exported certificate in a text editor such as Notepad, we'll need its contents for the next step.
Go to the SAML settings page on FOSSA. In the "Identity Provider Single Sign On URL" field, enter the URL for your ADFS server with the path /adfs/ls at the end. In the "Certificate" field, copy in the certificate from the previous step. Then click "Save Changes" in the top right.
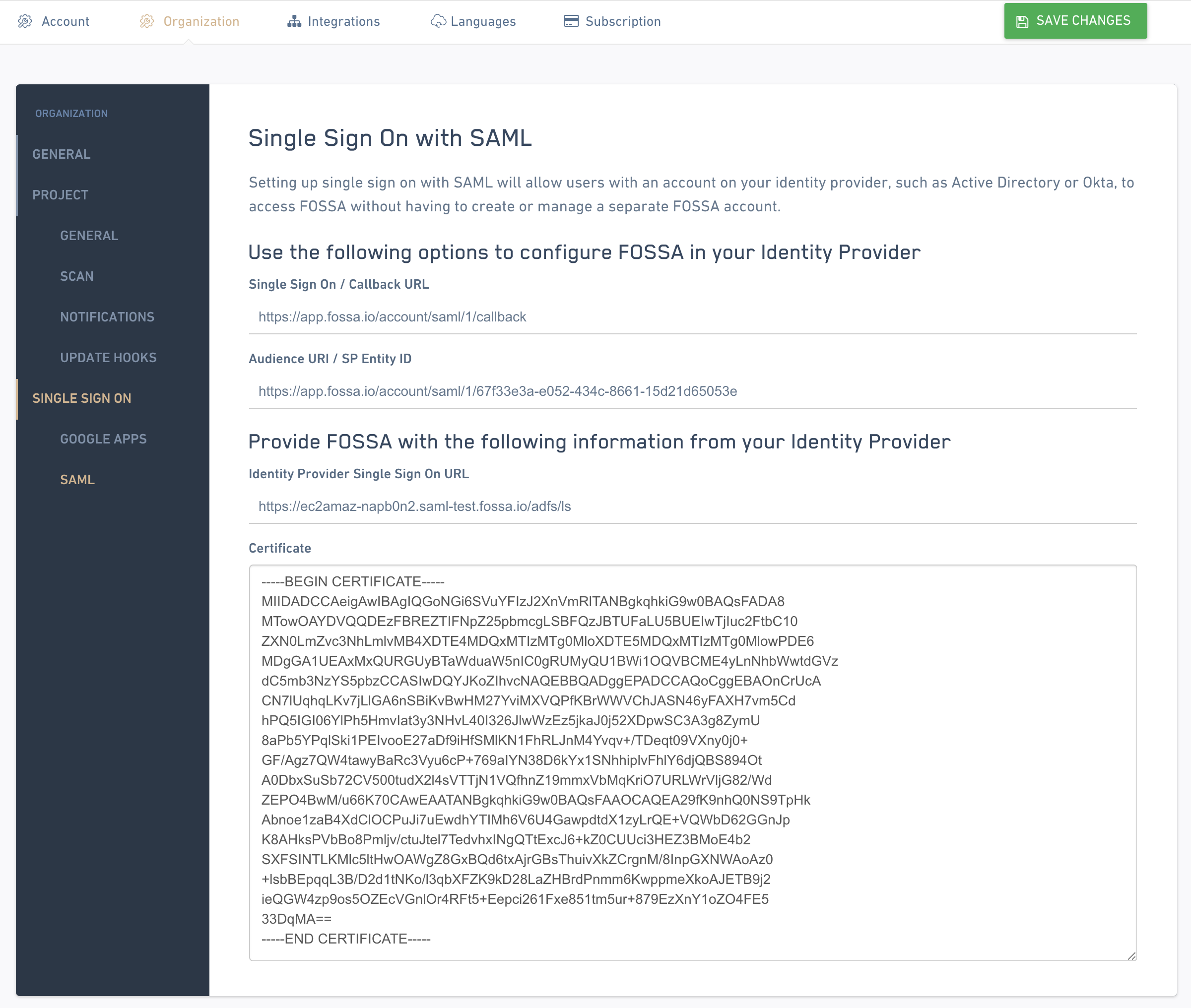
Congratulations, you're good to go! For their first log in, your users will have to log in either by visiting the "Single Sign On URL" from the SAML settings page with /callback removed or /adfs/ls/idpinitiatedsignon on your ADFS server if you have that option enabled. Afterwards, they can log in by entering their email address on the FOSSA login page.
Updated 7 months ago
