Remediation Guidance
The Remediation Guidance report is a project level report intended to provide developers a vulnerability prioritization plan with a focus on remediating the most impactful security issues with the least amount of refactor effort. The report consist for four categories:
- Quick Wins
- High Priority Fixes
- Low Priority Fixes
- Outdated Dependencies
The primary distinction between this plan and the remediation guidance offered for individual security issues is the context used in calculating remediations. Specifically this report calculates remediations in the context of all active vulnerability and upgrade recommendations for the entire project, and any vulnerabilities potentially introduced by a given upgrade. As compared to individual security issues which provide the best remediation path of a specific CVE or vulnerability.
Recommended Upgrades
FOSSA maintains a proprietary remediation algorithm that takes into account vulnerability ignore rules, any vulnerabilities introduced by a potential upgrade, and other remediation metadata aggregated across our knowledge base. Our remediation engine is designed to avoid recommending upgrades that would worsen your overall security posture. For instance, if the nearest patch version introduces similar or more severe vulnerabilities, FOSSA will suggest a more secure upgrade path—even if it requires a larger version jump—to ensure an overall improvement in your security posture.
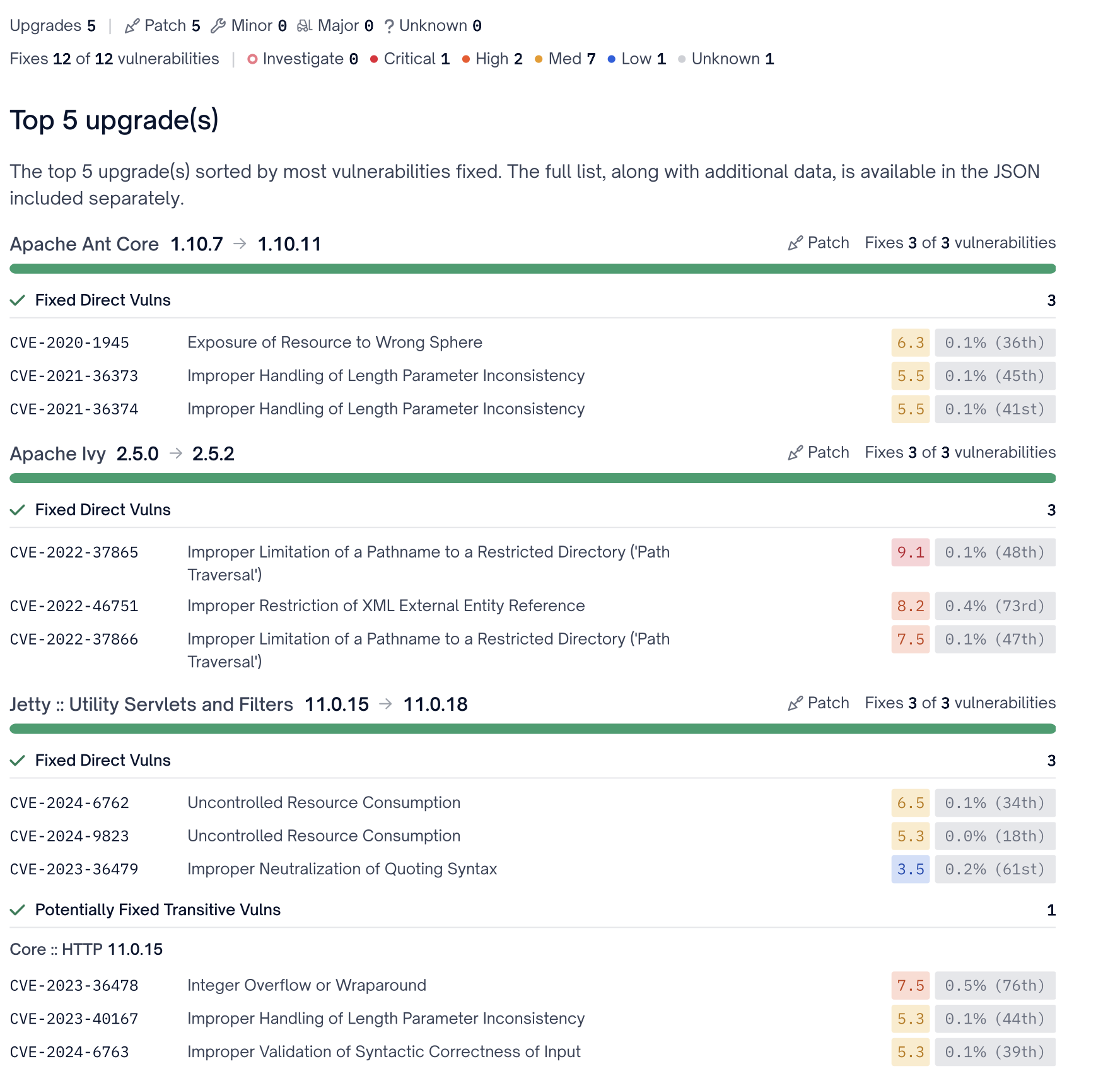
Quick Wins
The Quick Wins category limits remediation recommendations to patch upgrade distances as defined by semantic versioning. The intention of this category is to group vulnerability recommendations that can be easily resolved as they should not introduce breaking changes.
Quick Wins should be the first upgrade recommendations a development team prioritizes.
High Priority Fixes
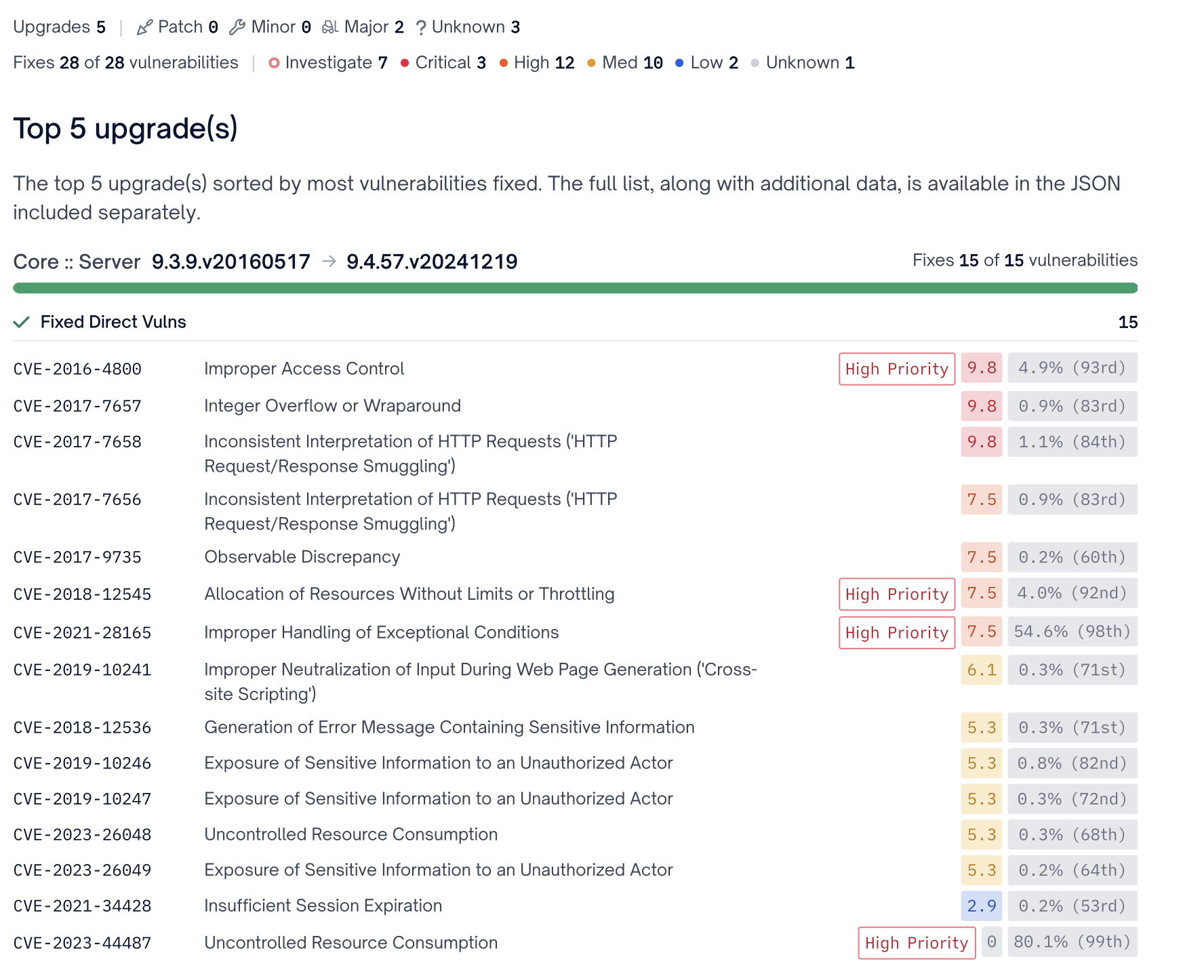
The High Priority Fixes category approaches vulnerability remediation by first leveraging FOSSA's exploitability prediction algorithm to calculate and flag true positive security issues, or those most likely to be exploited by threat actors. At a high-level this calculation takes into account various vulnerability metadata such as the CVSS vectors, exploitability data sources, static analysis based vulnerable function reachability, EPSS probability, and our own knowledge base to determine high priority vulnerabilities.
Next, FOSSA then uses our remediation algorithm to group all other security issues that may be remediated with the guiding principle of remediating the most impactful security issues with the least amount of refactor effort. A user may choose to include transitive vulnerabilities, by toggling the Transitive Vulnerabilities flag, that may be remediated by a given upgrade distance.
High Priority Fixes should be the second group of upgrade recommendaitons a development team prioritizes
Low Priority Fixes
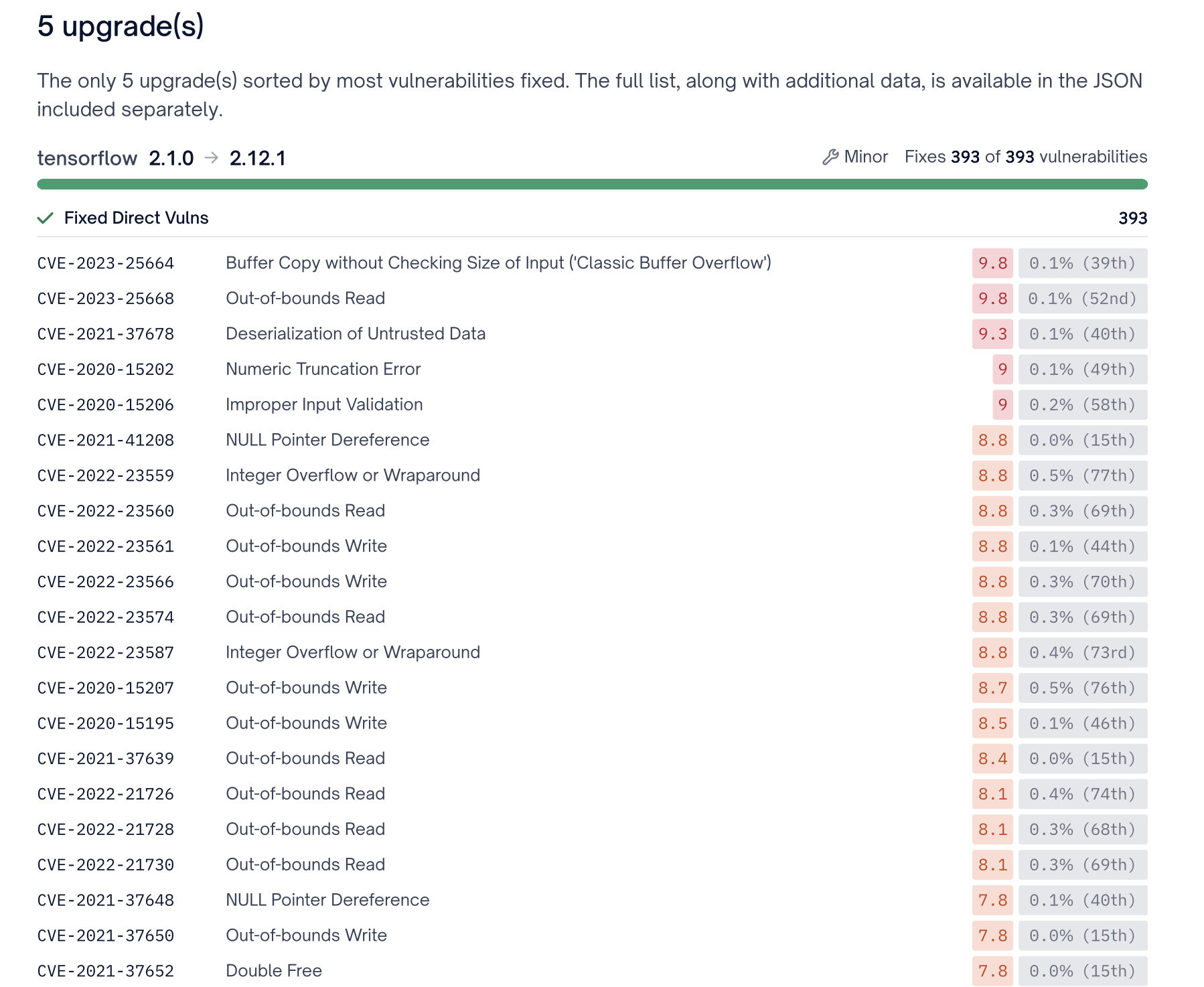
Any remaining vulnerabilities that were not flagged by the High Priority Fix calculation, but still meet the thresholds necessary by our recommendation algorithm will be grouped in the Low Priority Fix category. These are still real vulnerabilities that must be remediated by development teams, however should be prioritized after Quick Wins and High Priority Fixes. FOSSA will continue to group and assess vulnerabilities in this category ensuring we provide only recommendations that improve your overall security posture.
Low Priority Fixes should be the third group of upgrade recommendations a development team prioritizes.
Outdated Dependencies
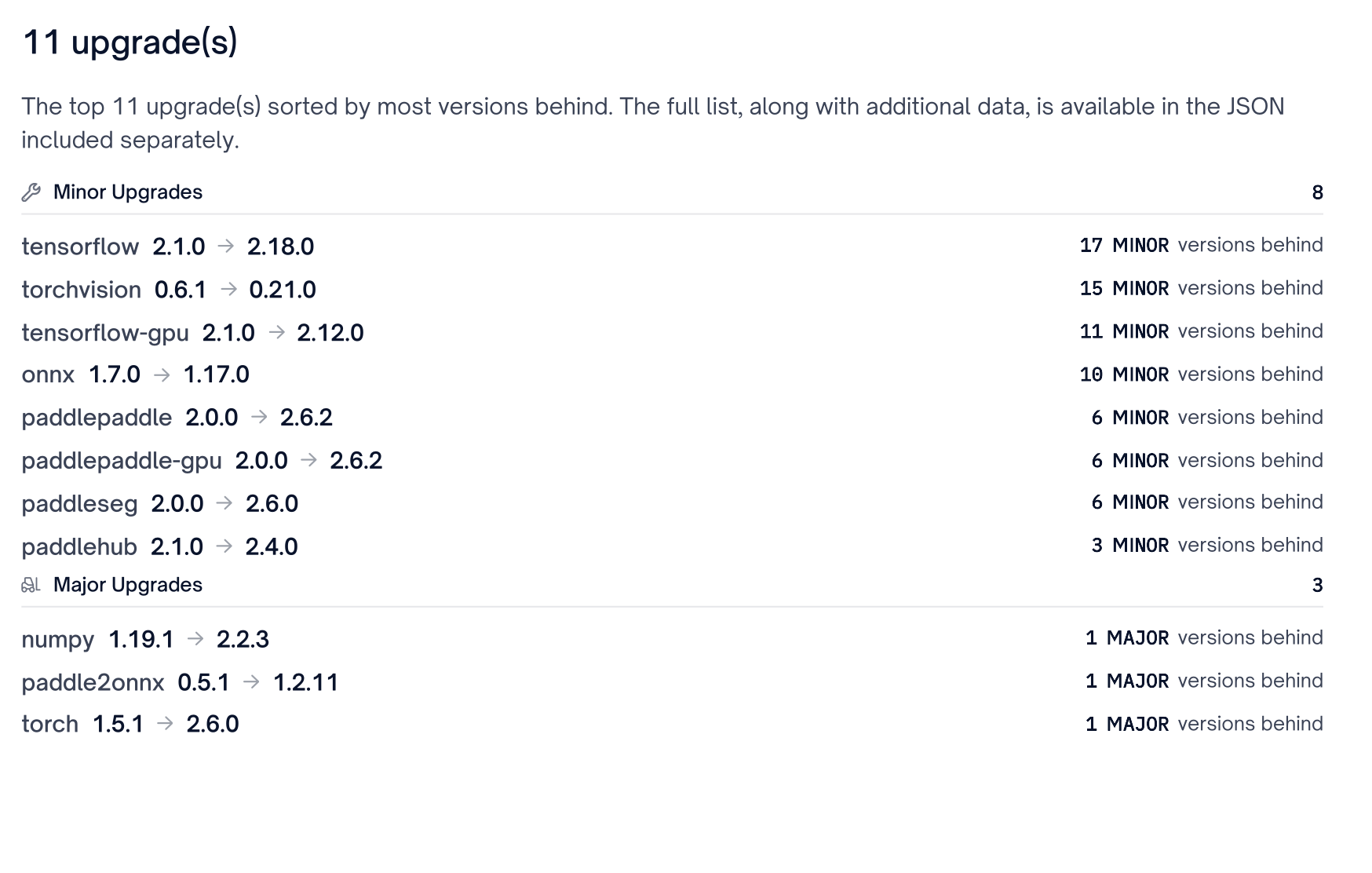
The Outdated Dependencies category is intended to provide development teams proactive recommendation guidance for dependencies that may cause major refactor pain if a high priority vulnerability appears in the future.
These are dependencies that are X patch/minor/major upgrades behind the latest release of a given package. Dependencies flagged in this category are determined by the projects Outdated dependencies policy. Please see Create Quality Policies for more details on configuring outdated dependencies. A user may choose to limit this category to only dependencies that do not currently contain vulnerabilities by toggling the Exclude Vulnerable flag.
Outdated Dependencies should be the last group of upgrade recommendations a development team should prioritize
NoteDue to the nature of dependency graph resolution the Transitive Vulnerability guidance asserts security issues that may , but are not confirmed, to be remediated by a given direct dependency upgrade. As compared to direct dependency guidance which will be remediated.
Formats
The Remediation Guidance report is supported in three formats:
- HTML
- JSON
NoteEvery remediation guidance report will include a json output of the full report including vulnerability details not included in the PDF & HTML outputs. The PDF & HTML outputs will contain the top 5 upgrades per category
Updated 7 months ago
